While I was working on a walkthrough on authentication and authorization I decided to use the Microsoft Graph API as an example. In this example I wanted to use application permissions to list all users. Nothing special. Configured my application, wrote some code but… got an error message telling me that my application does not have the required permissions to read all users. So let’s go back to Azure and verify the permissions.
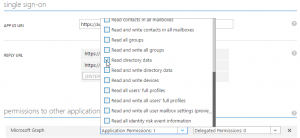
Looks pretty good. I actually do have some experience with authentication and authorization – which is why I’m writing this walkthough – but I do not have a clue about what I did wrong. No warning messages here. OK then, let’s search… and GitHub?! contains the answer. It appears that Microsoft decided that besides the permissions given by the administrator, the service principal also needs to be a “Company Administrator” (which you cannot configure from the UI) as a security measure. So the UI is just complete bogus without that role being assigned first. And another hour of my time is down the drain…
UPDATE:
To be consistent with not being consistent Microsoft does allow you to fetch all users if you use the BETA API (https://graph.microsoft.com/beta/users) as security in a public BETA – that is automatically enabled for everyone – apparently is not that important.